JerryG-OSM
I like the disclaimer that often appears on computer data sheets. "No one computer can provide absolute security under any circumstances." This statement is correct, but many military and aerospace computing platforms have to deal with extraordinary tasks. The important applications needed must be secure. Intruder intrusion can cause the task to fail. The increasing mobility of electronic platforms has made the challenge even more daunting. What are the main issues designers need to pay attention to when developing an embedded platform? How to reduce the risk of security intrusion?
Computers in military and aerospace applications range from IT to drones. The server technology used in IT applications has established a good security infrastructure, but many embedded computer platforms in drone applications do not use a lot of IT technology. In the past few years, protecting real-time, embedded platforms is an important priority because each system is isolated. But now, as more data is transmitted and stored in the form of electronic data, security is extremely important in embedded computing platforms. Platforms have become more intelligent, connections are more tight, and wireless networks are particularly vulnerable, so the focus on security issues has become more prominent.
safe question
Security issues are very important topics and it is difficult to decide where to begin. I can't make a full comment, but at least I can make sure you understand the basics. As stated in the statement, risks are everywhere. When you think you have a security system, some people have discovered loopholes and destroyed your platform. Without a fully isolated system with the highest degree of caution, the security system is just a dream. But understanding the types of security threats can at least help set some priorities and manage risk.
Frank Stajano used effective taxonomy in his book "The Security of Pervasive Computing," published by John Wiley, and classified computer security threats based on whether they threaten confidentiality, integrity, and availability. For the three categories. Decomposing security into these parts makes assessment of potential solutions easier and more effective.
Stajano described that unauthorized disclosure of information to unauthorized users (possibly unrelated individuals or computing devices) violates confidentiality; if unauthorized information is changed, Violated by integrity, it may change the transmission between hosts or devices; Availability refers to the system's constant acceptance of authorized users' legal requirements. Attackers often successfully reject legitimate users' services by occupying all available resources, which violates usability.
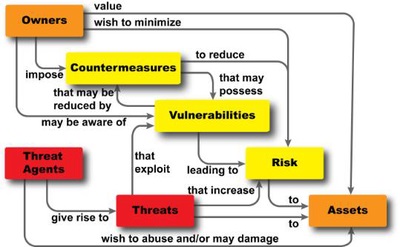
Security Risk Management
hardware
From the hardware and software layer to the terminal application, security issues are very important. To ensure maximum system security, every step is important. To manage risk, you must be sensitive to the security threats of the entire system architecture. Security starts at the processor. A basic or trusted root must be established to provide security services for establishing a strong security environment. Intel vPro technology was introduced in 2006 and was later updated with several new features. It provides a strong foundation for the establishment of security systems, most of which have been published on Intel vPro technology, and I leave it to you for further study.

Intel® vProTM Technology Overview
BIOS
The next layer of defense is in the BIOS layer. The threat of attacks on the BIOS is gradually increasing. Intrusion reports are also becoming more and more common. The National Institute of Standards and Technology (NIST) has released new safety guidelines for dealing with BIOS updates that pose the biggest security threat. According to the requirements of the new safety guidelines NIST SP 800-147, NIST sets standards and requires verification of the BIOS update mechanism.
BIOS vendors have taken serious and stringent measures to address security challenges and provided multiple sets of products with multiple layers of security defenses. They support the latest Intel vPro technology, allowing users to efficiently manage, inventory, diagnose, and repair their systems efficiently, remotely, and streamlined without compromising system security. BIOS vendors support NIST SP 800-147 guidelines and they offer a variety of other security options to protect FLASH and other storage devices. Users can easily place their security responsibilities on the hardware and BIOS level as much as possible because the security defense is the strongest.
Phoenix Technology's Phoenix SecureCore has a powerful set of security support. US MiGratere (AMI) and its Aptio V UEFI BIOS compatible products provide UEFI secure boot to enhance platform security.
operating system
The operating system has played a large role in providing a higher level of security. The recent introduction of multi-core processors has enabled multiple operating system instances to run on a multi-core processor, increasing operational flexibility and facilitating the creation of hypervisor architectures that protect key elements of the software environment. Real-time operating system vendors have made the hypervisor a key part of the product portfolio.
Green Mountain Software illustrates the importance of security to operating system vendors through an example. They have a dedicated business unit - the INTEGRITY Security Services (ISS) business unit, to address people's needs for higher-level security software. ISS has equipped the INTEGRITY operating system with a toolkit that provides reliable and effective security software to ensure that these ubiquitous embedded devices are in a safe state.
The ISS toolkit was developed based on Green Mountain's proprietary Federal Information Processing Standard (FIPS) compliant encryption toolkit. The ISS encryption toolkit complies with the latest government standards and utilizes potential FIPS encryption primitives to enable users to use the security protocol with full permission. The kit's design requirements are small, scalable, and certified by the U.S. government. Universal operating system that supports Windows, Linux, VxWorks, INTEGRITY, and Intel processors.
ISS focuses on:
Authentication - The process of identifying users, devices, and software on the network.
Authorization - Authorize users and devices to access resources and perform specific operations.
Network Access Control - This mechanism only allows authenticated and authorized devices, software, and users to access the network.
Confidentiality - Use passwords to convert data so that the data is readable only by authenticated authorized users.
Integrity – This inspection mechanism is used to detect unauthorized changes in the data transmitted in the device, software, and data lifecycles.
Remote Management - Methods for remotely monitoring, updating, and managing manufacturing and dispatching equipment.
Provide end-to-end security solutions
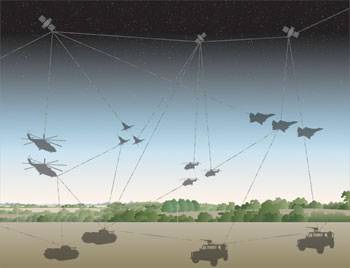
Creating related battlefields is very important for our team's victory. As the diversity of data is transmitted over more equipment and vehicles on the battlefield, the requirements for higher confidence and portability encryption kits are critical.
to sum up
Despite the large amount of software used to prevent computer and network attacks, these attacks are continuing to spread. Establishing a strong digital identity for users and computer systems through hardware-based security is an important step in breaking through the software strategy. Defensive organizations have made space security a top priority. Using more COTS in defense plans increases the reliance on Intel Smart Systems Alliance members and their products. As the defense system is transformed into an intelligent system, security protection will not stop. Once new violations are discovered, they will be resolved with new technologies.
Philizon enjoys a high reputation in Grow Light and Aquarium Led Light fields throughout Europe and America, Philizon also insists on taking high technology to design the newest&best Industrial Grow Light and aquariumlight constantly as the market request. Our R&D team with more than 10 people has rich experience in appearance design, electronic structure,heat dissipation simulation analysis, optical lens design, lightcontrol system etc. Most of our hydroponics full spectrum Led Grow Lighting and marine coral reef ledaquarium lighting are private modules,we have 10 more design patent and utility model patent till now.
Our Industrial Grow Light is popular in led market, cause its elegant outlook and its high quality and competitive price.


What is Full spectrum led chip ?
It is the newest trend for indoor plants. Advanced Led Grow Lights chip,not provide sigle color ,provide broad spectrum 400nm~840nm,simialr with sun light ,but most is red and blue,it is best for plant grow.This is a revolutionary step for Grow light which have previously been unable to act as the sole light source for the indoor garden.Suitable for all stages of plant growth.
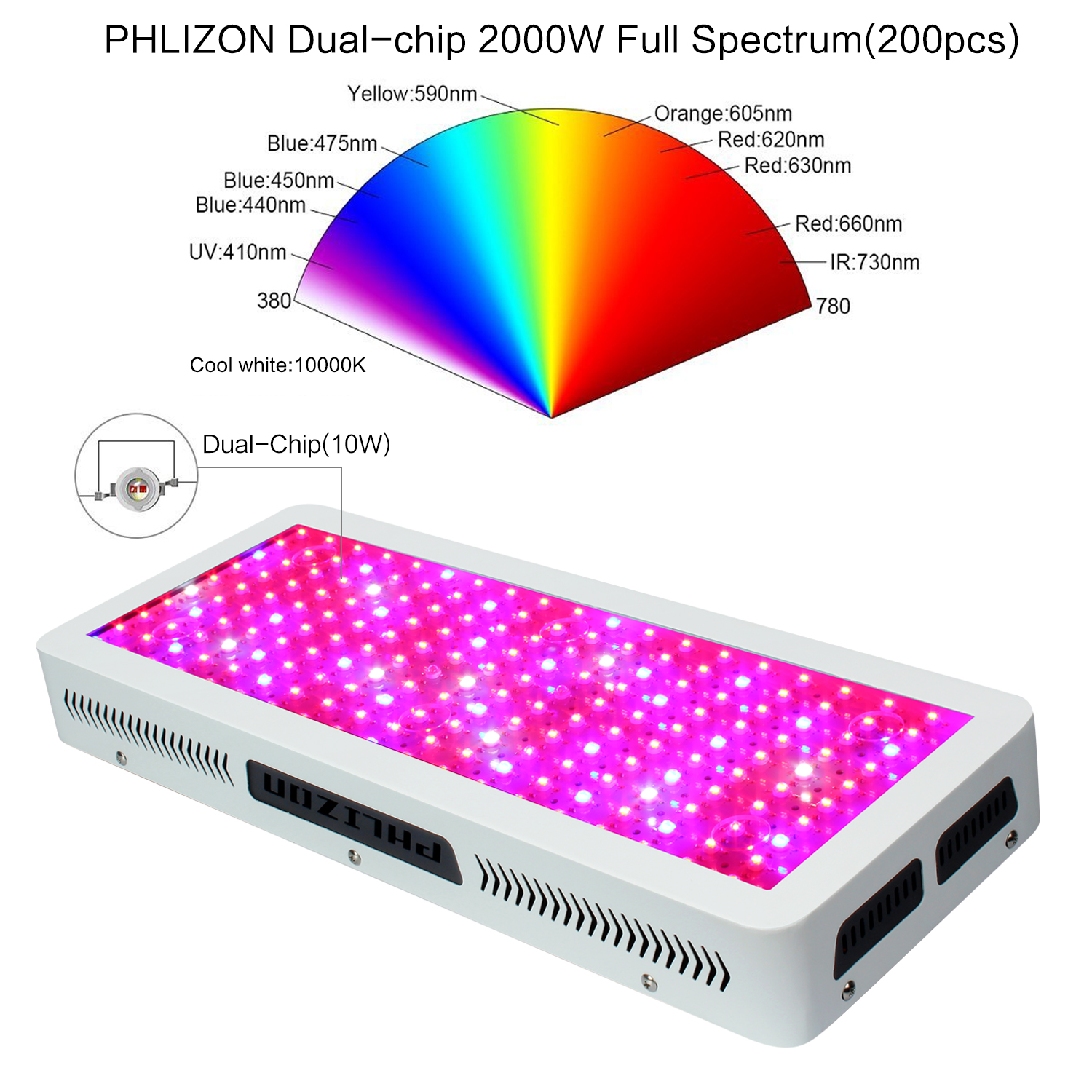
Advtanges:
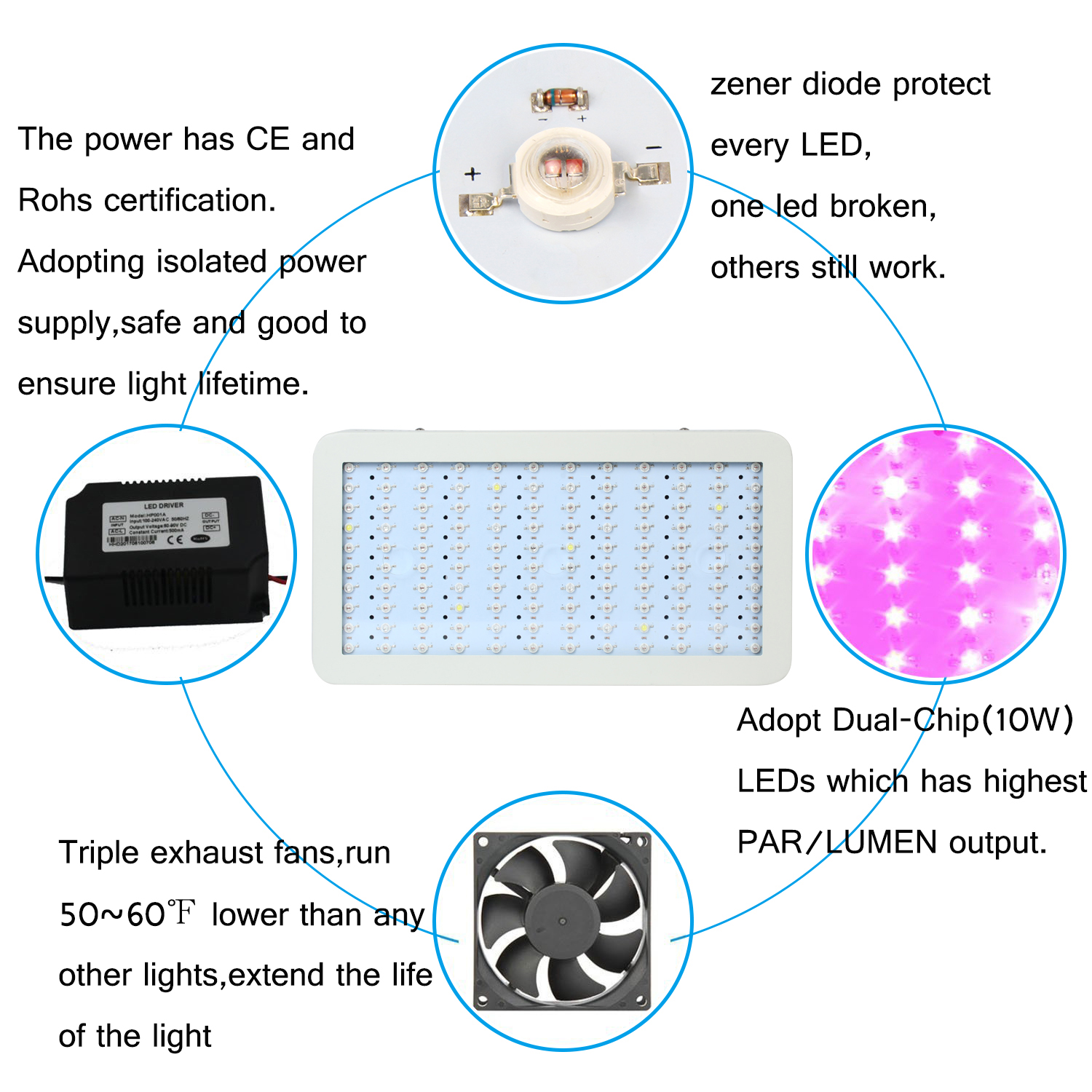
Upgraded Epistar chips,High Lumen,High penetration.
Plug with listed certificate safe to use.
The Plug you can choose
Ageing Test

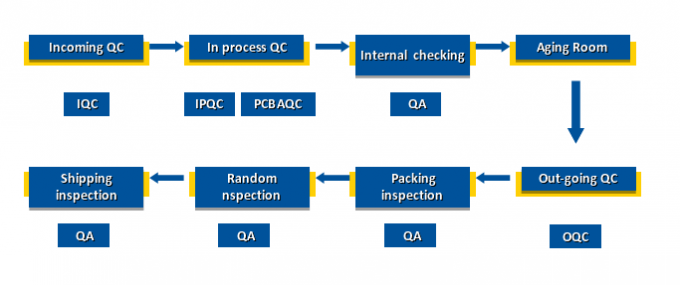
Our Quality Control systems
Package


Our professional Square Grow Light are suitable for all the indoor plants and good for seeding, growth,flowering and fruiting stages of plants, increasing the harvest and Saving energy.

Warnings:
1.lndoor use only.
2.To avoid being damaged,do not use water or drip irrigation while using.
3.Sunshine lighting time should be 12-18 hours.
4.While irradiating the plants,the height of led grow lamp is not less than 10 inches,low height will cause the destruction of plants.
5.Highly hang the lamp will weaken the energy and affect the growth cycle of the plants, so the lamp should not be hung too high.
6.While taking care of the plants, please spray the leaves and branches 2-3 times everyday,to ensure the the plants do not wrinkle a wither, and have no phenomenon of few fruit, and hard pericarp.
Our Company


Trade Terms
Payment: T/T, L/C, Paypal, 30% deposits before production, 70% balance to be paid before deliverying(Western Union are welcome)
Sample will be delivered within 7 working days.
Discounts are offered based on order quanlityes.
MOQ:sample order are acceptable
Delivery ways:DHL,UPS,FedEx,TNT, door to door,by sea,by air,etc.
Philizon Industrial Grow Light are perfect for green house applications and much more!
Led Commercial Grow Light,Led Grow Lights,Flower Plant Led Grow Lights,Fruits Plants LED Grow Light
Shenzhen Phlizon Technology Co.,Ltd. , https://www.philizon.com